In today’s ever-evolving threat landscape, security analysts face a constant barrage of alerts and data. Sifting through this information to identify genuine threats can be a time-consuming and overwhelming task. This is where Artificial Intelligence (AI) steps in, offering a powerful solution for security teams.
In this blog post, I’ll explore how AI-powered security information and event management (SIEM) solutions like Azure Sentinel can revolutionize your threat detection capabilities. Through a real-world case study, we’ll see how AI can automate tasks, uncover hidden threats, and empower security analysts to focus on what matters most – incident response and remediation.
The Power of AI in Azure Sentinel
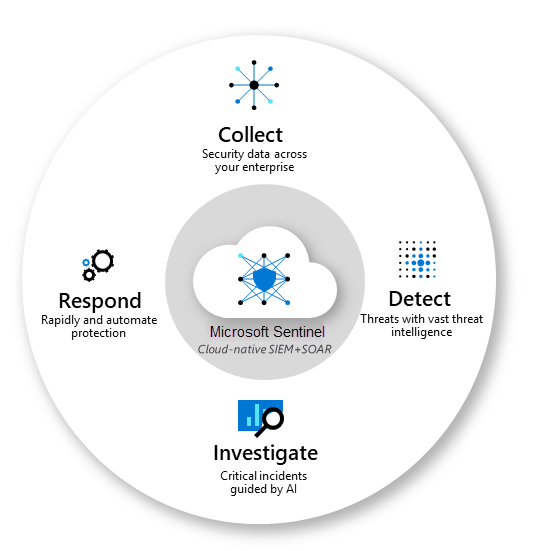
Azure Sentinel utilizes machine learning (ML) algorithms to analyze vast amounts of security data collected from various sources. This data can include firewalls, endpoints, user activities, and more. By analyzing this data, Azure Sentinel can:
- Identify Anomalies: AI can detect subtle deviations from normal behavior, potentially indicating a security breach.
- Prioritize Alerts: Instead of being flooded with low-priority alerts, security analysts can focus on high-risk incidents flagged by AI.
- Automate Threat Hunting: AI can continuously scan for suspicious activity, freeing up analysts’ time for deeper investigations.
- Predict Attacks: Machine learning can identify patterns and predict future attacks, allowing proactive security measures.
A Case Study: AI Detects Unusual Login Activity
Let’s consider a scenario where a company utilizes Azure Sentinel. An employee working late logs in from an unfamiliar location at an odd hour. This triggers an alert in Azure Sentinel. However, instead of simply notifying the security team, AI analyzes various factors:
- The employee’s typical login location and times.
- Their access history and recent activity.
- Geolocation data associated with the login attempt.
Based on this analysis, AI might determine the login attempt to be high-risk. It could then:
- Notify the security analyst: Highlighting the suspicious activity and providing relevant details.
- Trigger a multi-factor authentication request: Adding an extra layer of security for the login attempt.
- Block the login attempt: If the risk score is high enough, AI could take immediate action to prevent unauthorized access.
This scenario showcases how AI in Azure Sentinel can identify potential threats that might slip through traditional rule-based security systems.
The Benefits of AI-Driven Security
The advantages of using AI in Azure Sentinel are numerous:
- Improved Threat Detection: AI can uncover hidden threats and anomalies that might be missed by human analysts.
- Reduced Alert Fatigue: By prioritizing alerts and automating tasks, AI frees up analysts’ time for more strategic work.
- Faster Incident Response: With AI providing real-time insights, security teams can respond to threats quicker and more effectively.
- Enhanced Security Posture: Proactive threat hunting by AI helps organizations stay ahead of evolving cyberattacks.
AI is no longer science fiction; it’s a powerful tool readily available for security teams. By leveraging Azure Sentinel’s AI capabilities, organizations can gain a significant advantage in the fight against cybercrime. AI can automate mundane tasks, identify hidden threats, and empower security analysts to focus on what matters most – keeping your data and systems safe.
This is just a glimpse into the potential of AI in Azure Sentinel. As AI continues to evolve, so too will its capabilities in the realm of security. By embracing AI, security teams can ensure they are well-equipped to face the ever-growing challenges of the cyber threat landscape.